Introduction
Recently I put together an Intune configuration profile for a Single App Kiosk on the Samsung Galaxy Tab A8. After I got it working, in the way the client wanted it working; I did investigate how I could reset the device from the tablet itself. It looked to be impossible: indeed I was under the impression that meeting this particular requirement, that is, to reset the tablet from the tablet itself and not from the MEM portal, was addressed with the multiple app kiosk option.
I did however, find a way of resetting the device from the tablet in single app kiosk mode using the Power Button and the Side Keys feature. Now I don't know if this is by design or by happenstance, but it is something that is potentially a security exploit, and therefore needs to be addressed. And so this article will detail how you can reset an Android Tablet device in Single App kiosk mode, from the device itself. And it will detail the configuration setting that will prevent users from tinkering with this potential exploit. In addition it will briefly outline the construction of the profiles and apps used to create the kiosk.
The Kiosk Tablet Configuration
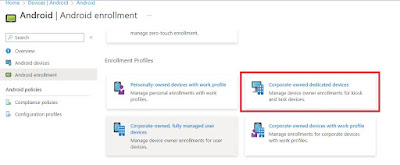
I will briefly outline the profiles instrumental in creating this particular kiosk build. Starting with the Android enrolment profile we use a Corporate-owned dedicated device profile.
When the tablet is removed from its packaging and powered on, we tap the language selection screen five times to begin a QR code enrolment. Using the tablet's camera we lock onto the QR code, and we complete the enrolment and setup experience. The machine is automatically added to an Intune group based on the name of the enrolment profile. This happens because the dynamic membership rule for this group uses the enrollmentProfleName property.
This works nicely and we can therefore assign to this group our configuration profiles. The app for this single app kiosk is Google Chrome:Fast & Secure and so this app is assigned to this group.
The website that is presented as the screen for the kiosk is configured as a Managed Google Play web App. This ensures that the user cannot open additional tabs on the Chrome browser.
The configuration profile that actually sets the tablet as a kiosk is a device restrictions profile. In the profile we specify the Managed Google play web app and we also define a single app for the kiosk mode requirement.
How a user can exist Kiosk mode with this Configuration
And of course the whole purpose of the kiosk is a lockdown so that users cannot tamper with the device, creating additional support costs and potentially creating a passage to a security exploit. Unfortunately a user is able to escape from the bounds of the Kiosk with this configuration. Here is how it is possible.
1) The user presses on the Power Button on the side of the tablet.
4) With the app selected as the side key app, it would appear that the user has no option but to go back to the kiosk. However if the user double clicks on the power button on the side of the tablet, after returning to the kiosk mode, the selected side key app appears. In my case this was the settings app and so I was able to perform a factory reset.
How to Close this Exit Route
In the Device Restrictions profile expand General Settings and scroll down to Dedicated devices. Set the Power button menu to Block.
Note: The above setting may result in the provisioning getting stuck in the policy synching phase of the tablet build. This is probably because a restart is required and the above setting may be preventing the restart. You can initiate a restart from the MEM portal to progress to the kiosk built stage.
Conclusion
This blog shows you should spend some time examining the tablet build for possible exploits. Thankfully in this case there is no need for too much concern because we are able to lock down the power button. I hoped you enjoyed reading this blog and I wish you success with your own Kiosk configurations.














No comments:
Post a Comment