Introduction
Oftentimes an IT administrator is concerned with getting an application ready for installation, without as much concentration on the application's uninstallation procedure. And if the administrator has specified an uninstall command line then this might be in consideration for an application upgrade. Uninstall old version and install new version. But most vendors are keen to have their applications easily upgraded and so their setup files will cater for the upgrade requirements as well as the new install requirement. And sometimes an unattended uninstallation is more difficult to achieve than the installation.
Yes the focus is sometimes mainly on installation, however equal focus should be on the uninstallation. Some applications are no longer fit for purpose, or their features have fallen behind their competitor's product, or the business model has changed and the application is no longer required, or the application presents a security risk to the organisation - in these situations the IT administrator needs an uninstallation process as robust as the installation process.
Microsoft's Configuration Manager product treats the uninstallation deployment the same way it treats the installation deployment. It is just another command line to be executed on the user's device - and success or failure is determined by whatever condition has been created to flag a successful installation of the applications. This could be a file or folder, or an MSI product code - when this installation condition fails for an the application uninstall deployment evaluation then, paradoxically, the uninstall deployment is a success.
Thus the administrator needs to spend as much effort on the management, administration and testing of the uninstall deployment as he or she does on the install deployment. And this is not always a wasted expenditure because another reason for uninstalling a product may be to save on licensing expenses, or to free up a license, no longer required on a machine, so that another users can take make use of the license.
Microsoft has implemented the implicit uninstallation feature in the technical preview release 2106 of Configuration Manager. This means that all we have to do is remove a device from a deployment's collection and, providing the deployment type contains a satisfactory uninstall command line, the application is going to uninstall itself without the administrator having to create an uninstall deployment.
In this article I test this feature using the Sysinternals BGInfo64 tool as an example. I create a deployment to install the tool to the primary site server system itself. I then remove the system from the deployment's collection, force a machine policy retrieval, and observe the automatic uninstall of the tool.
The Sysinternals BGInfo64 Application
For my own testing I created a PSAppDeployToolkit package to install the BGInfo64 tool. I like to use this handy wrapper toolkit for most of my packaging tasks - it provides a standard command line for all installations and all uninstallations, as well as a set of logs written to the Window\Logs\Software directory. Thus I can easily determine if the application has actually started to install and the logs themselves help me with troubleshooting failures. It is beyond the scope of this article to detail how this toolkit works or how to use it, however I can say it is very straightforward to learn. You can download it at the following location.
https://github.com/PSAppDeployToolkit/PSAppDeployToolkit.git
Alternatively you can use use your own registered application for your testing. If this is the case then you might want to skip to the section titled The BgInfo64 Deployment Configuration for an Implicit Uninstall, if your primary purpose is to learn about Implicit Uninstall and how to configure the deployment.
My package does the following when it is deployed as an installation.
1) Creates a Sysinternals folder at c:\program files\
2) Copies Bginfo64.exe and Pstools.chm files into the above directory
3) Creates a Bginfo64.lnk shortcut file to Bginfo64.exe at c:\users\public\desktop
My package does the following when it is deployed as an uninstallation.
1) Removes the Bginfo.exe file from c:\program files\Sysinternals
2) Removes the Bginfo64.lnk shortcut file to Bginfo64.exe at c:\users\public\desktop.
If you are familiar with the PSApp toolkit and would like to replicate my Bginfo64 PSApp package then you can do the following.
1) Download the Sysinternals tools from:
https://docs.microsoft.com/en-us/sysinternals/downloads/sysinternals-suite
2) Extract the BGInfo64.exe and PStools.chm and copy them into the PSApp SupportFiles folder.
3) Edit the deploy-Application.ps1 script file to include the following in the Install section
New-Folder -Path "c:\program files\SysInternals"
Copy-File -Path "$dirSupportFiles\Bginfo64.exe" -Destination "c:\program files\SysInternals\Bginfo64.exe"
Copy-File -Path "$dirSupportFiles\Pstools.chm" -Destination "c:\program files\SysInternals\Pstools.chm"
New-Shortcut -Path "c:\users\public\desktop\Bginfo64.lnk" -TargetPath "c:\program files\sysinternals\Bginfo64.exe" -IconLocation "c:\program files\sysinternals\Bginfo64.exe" -Description 'Bginfo54' -WorkingDirectory "c:\program files\sysinternals"
4) Edit the deploy-application.ps1 file to include the following in the uninstall section.
Remove-File -Path 'c:\users\public\Desktop\Bginfo64.lnk'
Remove-File -Path 'c:\program files\SysInternals\Bginfo64.exe'
The BgInfo64 Deployment Type User Experience Configuration
In my test package I select Install for system as the Installation behaviour. I select Whether or not a user is logged on for the Logon requirement. I select Normal for the Installation program visibility. I then select Allow users to view and interact with the program installation tickbox.
The BgInfo64 Deployment Configuration for an Implicit Uninstall
Having created my PSApp toolkit package to install the Bginfo64 tool and having registered it in my primary site Technical Preview 2106 Configuration Manager instance as an application, and also having created the Deployment Type with the above configuration - the next steps are:
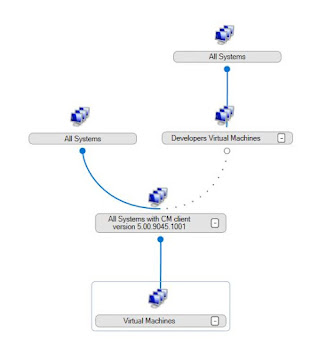
1) Create a collection and add the name of my primary site server into the collection as a Direct Rule.
2) Create a mandatory deployment to the collection with the option Uninstall this application if the targeted object falls out of the collection selected.
3) Force a machine policy by running the Machine Policy Retrieval & Evaluation Cycle action.
The Configuration Manager BGInfo64 package with Implicit Uninstall Executes
If you are testing your own application deployment then obviously the installation experience will be different. My PSApp BGInfo64 package manifests itself with an install log at c:\windows\logs\software. In addition, because I am logged onto the primary site server I am presented with the PSApp Deployment Toolkit wizard allowing me to defer the installation - and this is a rather handy feature and another good reason to use the wrapper for your packaging tasks.
I click on Continue and the installation completes. As can be seen, a shortcut to Bginfo64.exe appears on the desktop, the Sysinternals directory is created in c:\program files and the bginfo64.exe along with Pstools.chm files are copied into this directory. In addition the PSApp wizard thanks me for my patience and advises a reboot (not really required of course and you can customise this message as required).
I do click on OK but do not reboot my site server HyperV machine. We can now test the implicit uninstall feature.
Testing the Implicit Uninstall feature in Preview Version 2106
Now we are in a position to test the Implicit Uninstall feature, and this requires us to remove the direct membership rule, for the targeted machine, from the targeted collection. After this is done the following occurs:
1) Every 10 minutes a background worker process runs and detects devices the need to have implicit uninstall applications removed (because they have been removed from the install collection). The activity of this worker process is written to the SMS_ImplicitUninstall.log file on the primary site server.
2) The client performs a computer policy download - by default this is every 60 minutes.
3) 15 minutes later the implicit uninstall application is uninstalled.
In my test I remove direct rule for my device from the collection so that it is now empty.
I then force a machine policy refresh action on the device.
We can see the event triggered in the SMS_ImplicitUninstall.log file
I then complete an Application Deployment Evaluation Cycle.
Note: this last action is not detailed as necessary in the release documentation however it was required in my testing scenario.
As can be seen above, the Bginfo64 shortcut file is removed and the PSApp uninstall log created - this verifies that the implicit uninstall feature has succeeded.
Summary
The implicit uninstall feature is a great new addition to the Configuration Manager product. It simplifies the administration required to uninstall applications. It reduces the number of collections in Configuration Manager thus reducing processing overhead. Obviously care must be taken to ensure that devices are not accidently removed from installation collections. I look forward to seeing this new feature implemented in the current release version of Microsoft Endpoint Configuration Manager.
I hope you enjoyed reading this article and I wish you similar success in your own testing environments.
Colin