Introduction
There are various ways in which you can build a bridge between your on premise Configuration Manager infrastructure and your Azure cloud tenant. Understandably many administrators exercise great caution before making any major changes to their on premise management capabilities and will push back against any changes - until their confidence levels are high.
The cloud offers so many advantages in terms of mobile device management that push back is an approach no longer plausible - tenant attach is a great way to make a start. There is no requirement to already have a Cloud Management Gateway (CMG) configured. Setup requires only a few clicks of a wizard.
In this blog I take a very fresh Configuration build on preview 2005 and configure Tenant Attach. And again the Azure Tenant is also a fresh configuration. No clients are on the tenant and only three clients are on the on premise SCCM site - a the primary site itself and a DC both running Server 2019 builds 1808 and a Windows 10 client on build version 2004.
The SCCM site is not even configured for co-management and neither is it configured for PKI, although of course it should be. The point here is to illustrate the simplicity of the Tenant Attach feature.
Using the Configure co-management Wizard
1) Open the Configuration Manager console and navigate to Administration\Overview\Cloud Services\Co-management. Right-click and select Configure co-management. The co-management configuration wizard window appears. We do not want to enable co-management thus deselect Enable automatic client enrollment for co-management.

3) Click on Sign In and enter in your Intune account credentials, click Next and then the password and Next again. When the Sign in option is grayed out as shown you are ready to click on Next.
Uploads to the tenant will occur every 15 minutes.
Verify Machine Accounts in the Microsoft Endpoint Manager
Open your tenant Microsoft Endpoint Manager admin center and navigate to Devices\All Devices. Your SCCM devices should appear - in this case the three machines with an SCCM client are now showing in the portal. You can troubleshoot issues by examining the CMCSyncUploadWorker.log file on your primary site server.
There are various ways in which you can build a bridge between your on premise Configuration Manager infrastructure and your Azure cloud tenant. Understandably many administrators exercise great caution before making any major changes to their on premise management capabilities and will push back against any changes - until their confidence levels are high.
The cloud offers so many advantages in terms of mobile device management that push back is an approach no longer plausible - tenant attach is a great way to make a start. There is no requirement to already have a Cloud Management Gateway (CMG) configured. Setup requires only a few clicks of a wizard.
In this blog I take a very fresh Configuration build on preview 2005 and configure Tenant Attach. And again the Azure Tenant is also a fresh configuration. No clients are on the tenant and only three clients are on the on premise SCCM site - a the primary site itself and a DC both running Server 2019 builds 1808 and a Windows 10 client on build version 2004.
The SCCM site is not even configured for co-management and neither is it configured for PKI, although of course it should be. The point here is to illustrate the simplicity of the Tenant Attach feature.
Using the Configure co-management Wizard
1) Open the Configuration Manager console and navigate to Administration\Overview\Cloud Services\Co-management. Right-click and select Configure co-management. The co-management configuration wizard window appears. We do not want to enable co-management thus deselect Enable automatic client enrollment for co-management.
3) Click on Sign In and enter in your Intune account credentials, click Next and then the password and Next again. When the Sign in option is grayed out as shown you are ready to click on Next.
4) Click on Next. A message appears stating that an AAD application will be registered in your tenant. Click on Yes to create the AAD Application.
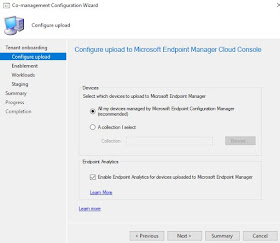
5) The Configure upload to Microsoft Endpoint Manager appears. Ensure that All my devices is selected (or a specific collection if you prefer) and also select Enable Endpoint Analytics for devices uploaded to Microsoft Endpoint Manager.
6) Click on Next. The Enable co-management window appears. In this exercise we do not want to enable co-management thus ensure None is selected for Automatic enrollement in Intune and click on Next again.
7) The Workloads window appears, again click on Next without modifying the defaults.
8) The Staging window appears. Click on Next to continue.
9) The Summary windows appears. Click on Next to complete the Tenant Attachment
Uploads to the tenant will occur every 15 minutes.
Verify Machine Accounts in the Microsoft Endpoint Manager
Open your tenant Microsoft Endpoint Manager admin center and navigate to Devices\All Devices. Your SCCM devices should appear - in this case the three machines with an SCCM client are now showing in the portal. You can troubleshoot issues by examining the CMCSyncUploadWorker.log file on your primary site server.